Free Encrypted Email Service[ Encryption Tools | Acceptable Use Policy | Add this resource page to your Favorites] [ Home | Network Tools | Encrypted Email Help | Get
a Secure Spam-Protected Address at CanadaEmails.com ]
Why Should I Use Encrypted EmailEstimates suggest that there are currently hundreds of persons using the internet who can read your confidential email messages when sent from an unprotected, non-encrypted email client. Spy agencies run by many national governments, including unfriendly ones, scan everyone's email! Bad guys do it too.You can prevent such snoopy eavesdroppers from reading your email by encrypting it.This is done by transforming your plain text message into hard-to-decode cipher text. About Our Free Encrypted Email ServiceThe aim of our service is to transmit your email text message in an encrypted form so that it cannot be parsed for key words while enroute. What happens once it is stored on the receiver's computer is up to them and the protective security measures they have enabled. Your e-mail remains encrypted from the time it is sent and
until it is received and decrypted by the intended recipient. The
recipient automatically receives instructions for decrypting
messages. No unencrypted message is transmitted across the
internet. Using our encrypted email service there is no need to exchange passwords or complex public key details with encrypted email recipients. The encrypted email recipients are automatically sent instructions for deciphering the encrypted email. Sending an encrypted email message using our service is as simple as sending an ordinary Web-Mail. Other email encryption methods require the sender and receiver to exchange public keys which is complicated, inconvenient and not very practical when sending encoded email messages in a spontaneous fashion. Email Encryption at MyComputerCop.com
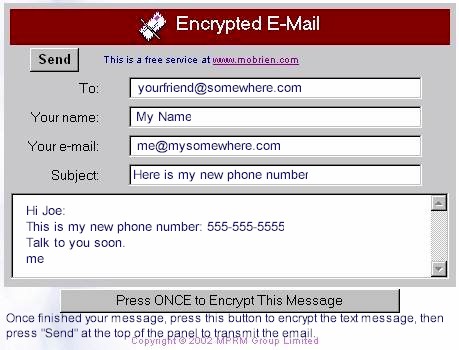
Once you have obtained a Temporary Password and clicked the button below, an email panel such as that illustrated above will open.
More About Encrypted EmailYou come to work or school one day to find that an FBI special agent has just paid a visit and that the system administrator has shut down your computer account to comply with a subpoena for all of your email and other computer files. One of "your" non-encrypted email files contains a large collection of credit card information or a "Nigerian Fraud Email" or a variety of scam projects or even all of these. Junk Mail? You did not create those non-encrypted email files and know nothing about it. You have been using hard-to-guess passwords and changing them regularly. How could someone have gotten access to your computer to use it for this scurrilous activity? How would the FBI or other agency find it? One likely possibility is that as well as being a recipient of a ton of spam or junk email, you have been a victim of an email packet sniffer attack. The information you transmit via email is essentially being sent back and forth along a wire. Anyone along that wire has the access enough to intercept and read the text. It's fairly easy to do. You might think that there would be an awful large amount of text information to scan. That's true, but the people doing the packet sniffing are looking for very specific key words. They program their "sniffing" software to perform certain actions and both store and flag messages containing certain key words. That's where encrypted email comes in. The words in your encrypted email are gibberish to such packet sniffers and the email passes unread by the eavesdropper. As your encrypted email travels to the destination mail server via as many as 30 hops from computer to computer, the various packet sniffers that intercept the encrypted email will only read sense from the to and from addresses. The encrypted email's message portion will pass by the eavesdropper unnoticed. Acceptable Use Policy For Encrypted EmailBy using this Encrypted Email service you agree to
our acceptable use policy and to respect the privacy of others.
Encrypted Email services must not be used for any improper
purpose. [ Home | Network Tools | Send Encrypted Mail | Encrypted Email Help ] |
||||||
| Computing | ||||||
| Our OpenPGP Key Server | ||||||
| DNS / NetTools | ||||||
| Detect Intruders | ||||||
| Email Encryption | ||||||
| Firewalls | ||||||
| Net Crime | ||||||
| Security Topics | ||||||
| Traceroute | ||||||
| Network Tools |